Cybersecurity threats are evolving at an unprecedented pace, fueled by advancements in artificial intelligence, the proliferation of connected devices, and the growing sophistication of cybercriminals. For individuals and businesses alike, staying informed is no longer optional—it’s a necessity. In this article, we dissect the most critical cybersecurity threats poised to dominate 2025 and provide actionable strategies to safeguard your digital assets.
Table of Contents
Understanding Cybersecurity Threats in 2025
The digital landscape of 2025 is a double-edged sword: while innovation drives efficiency, it also opens new avenues for exploitation. Cyberattacks are no longer limited to isolated incidents; they now threaten national infrastructure, global supply chains, and personal privacy. Below, we analyze seven key threats and their implications.
1. Phishing Attacks: The Gateway to Data Breaches
Phishing remains the most pervasive threat, accounting for over 90% of data breaches (2023 Verizon DBIR). Attackers now leverage AI tools like ChatGPT to craft hyper-personalized emails, impersonating colleagues, banks, or even government agencies. For example, “CEO fraud” scams trick employees into wiring funds by mimicking executive communication styles.
New Trend in 2025: Deepfake phishing uses AI-generated voice or video to impersonate trusted contacts, making scams harder to detect.
2. Ransomware: Holding Data Hostage
Ransomware attacks have shifted from opportunistic to highly targeted campaigns. In 2024, a major hospital chain paid $10 million to restore patient records after attackers exploited unpatched VPN vulnerabilities. Worse, double extortion tactics now involve stealing data before encryption, threatening public leaks if ransoms go unpaid.
Industries at Risk: Healthcare, education, and critical infrastructure remain prime targets due to their reliance on real-time data access.
3. Advanced Persistent Threats (APTs)
APTs are stealthy, state-sponsored campaigns aimed at espionage or sabotage. The 2023 breach of a defense contractor, attributed to a nation-state group, exposed blueprints for advanced weapon systems. These attacks often persist undetected for months, using custom malware and zero-day exploits.
Defense Strategy: Network segmentation and behavior analytics tools can flag unusual activity, such as abnormal data transfers at odd hours.
4. IoT Vulnerabilities: A Growing Concern
By 2025, over 75 billion IoT devices will be in use globally, yet many lack basic security protocols. In 2024, a smart thermostat vulnerability allowed hackers to infiltrate a corporate network, leading to a massive data leak. Industrial IoT (IIoT) devices in manufacturing and energy sectors are particularly vulnerable to sabotage.
Case Study: The Mirai botnet attack in 2016 hijacked 600,000 IoT devices to launch DDoS attacks—a risk that persists with poorly secured gadgets.
5. Cloud Security Threats
Misconfigured cloud storage buckets exposed 30% of enterprises to breaches in 2023 (Gartner). Shared responsibility models often lead to confusion: while providers secure infrastructure, users must manage access controls. For example, an employee accidentally setting an AWS S3 bucket to “public” could leak sensitive customer data.
Solution: Tools like Cloud Security Posture Management (CSPM) automate configuration checks and enforce compliance.

6. Insider Threats: The Enemy Within
Insider threats—whether malicious or accidental—are notoriously hard to detect. A 2025 incident involved a disgruntled IT admin deleting critical databases before resigning. Conversely, employees clicking malicious links in phishing emails account for 60% of accidental breaches (Ponemon Institute).
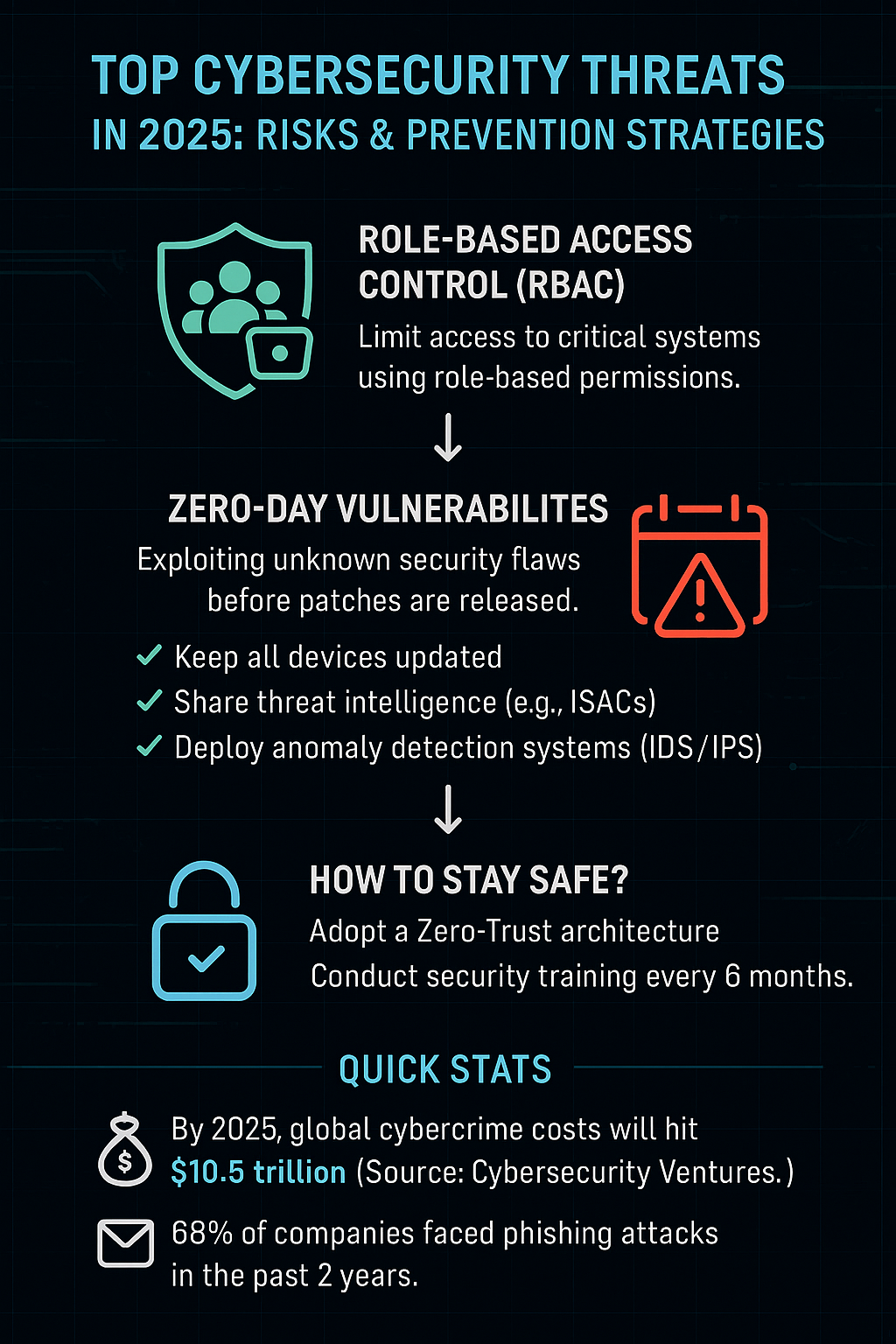
Mitigation: Implement role-based access controls (RBAC) and monitor user activity with tools like Microsoft Purview.
7. Zero-Day Exploits: The Silent Killers
Zero-day exploits target unknown software vulnerabilities, giving developers no time to patch. The 2024 MOVEit breach exploited a zero-day flaw to steal data from governments and corporations. Dark web markets now sell zero-day exploits for upwards of $1 million, attracting both criminals and nation-states.
Proactive Defense: Threat intelligence platforms like Recorded Future track emerging exploits, enabling preemptive action.
How to Protect Against Cybersecurity Threats in 2025
Combatting modern cyber threats requires a multi-layered approach:
Backup Critical Data: Follow the 3-2-1 rule: 3 copies, 2 storage types, 1 offsite. Test backups regularly to ensure quick recovery.
- Adopt Zero-Trust Architecture: Assume breaches will occur and verify every access request. Use micro-segmentation to limit lateral movement in networks.
- Prioritize Patch Management: Automate updates for OS, software, and firmware. The 2024 Equifax breach stemmed from an unpatched Apache Struts flaw—a preventable oversight.
- Train Employees Continuously: Conduct simulated phishing drills and teach staff to recognize deepfake scams.
- Leverage AI-Powered Tools: Deploy solutions like Darktrace or CrowdStrike Falcon to detect anomalies in real time.
Phishing remains the most common threat, leveraging social engineering to deceive users into revealing sensitive information.
FAQ
What’s the most underestimated cybersecurity threat?
Insider threats. Employees with excessive access privileges can cause irreparable harm, whether through malice or negligence.
How can individuals protect smart home devices?
Change default passwords, disable unused features (e.g., remote access), and segment IoT devices on a separate network.
Is cybersecurity insurance worth it?
Yes, but policies often exclude acts of war or unpatched vulnerabilities. Review terms carefully and pair insurance with robust defenses.
Summary
The cybersecurity landscape of 2025 demands vigilance, innovation, and collaboration. From AI-driven phishing to IoT sabotage, threats will continue to evolve, but so will defensive technologies. By adopting zero-trust principles, investing in employee education, and leveraging automated security tools, individuals and organizations can stay one step ahead of cybercriminals.
Infographic listing top 2025 cybersecurity threats:
Final Thought: Cybersecurity isn’t just an IT issue—it’s a business survival skill. What measures will you prioritize in 2025?
What steps are you taking to protect yourself against these threats? Share your thoughts in the comments below!
